
The cautionary tales just keep coming for Internet-connected TVs, thermostats, and other so-called "Internet-of-Things" devices. Today's lesson comes courtesy of a smart TV from Vizio that was subjected to a man-in-the-middle attack because it couldn't be bothered to validate the HTTPS certificates of servers it connected to.
Researchers from security firm Avast found that the Vizio model in their lab broadcasted fingerprints of users' viewing habits, even when owners hadn't consented to a privacy policy displayed during set up. What's more, the researchers uncovered a vulnerability in the smart TV that could act as a potential attack vector for a hacker attempting to access a user's home network.
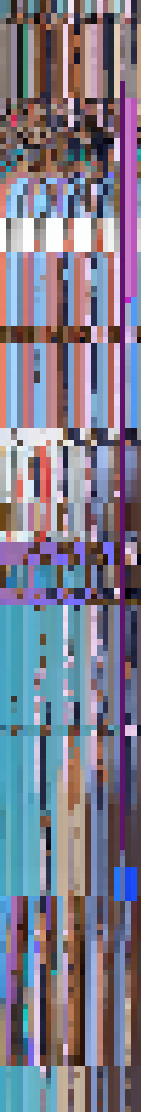
The researchers were unable to use traditional cracking methods to figure out what the salt was. So they instead used some reverse-engineering creativity to enumerate the entire file-system on the TV. They soon found a plain-text file that contained the salt (which they declined to name). They were then able to use their man-in-the-middle attack both to read data the TV sent to the server and to impersonate the server and send commands back to the TV. With that, they were able to decrypt the entire binary stream that traveled between the TV and tvinteractive.tv, which is operated by a company called Cognitive Networks.
In a blog post published Wednesday, the researchers wrote:
From this, it is obvious that the same data is being sent to Cognitive Networks servers through UDP and HTTP. This data is the fingerprint of what you’re watching being sent through the Internet to Cognitive Networks. This data is sent regardless of whether you agree to the privacy policy and terms of service when first configuring the TV.
Now, these points aren’t the full picture of what you’re watching. They are simply pre-defined points taken somewhere within the image viewable on the TV. Nevertheless, we can create a graphic representing this fingerprint over time, where each line of pixels represents a second in time, arranged top-to-bottom as oldest-to-newest:
Each horizontal line of various color blocks in the graphic represents averaged patches of color that the TV has captured from specific points of the image displayed on the TV screen.
Each successive line represents another capture in time. With this information, the content recognition service could match a record of these fingerprints from your TV screen to its own fingerprints of the broadcast to determine what you’re watching.
The image to the right represents a fingerprint of a Vizio smart TV owner's viewing habits. Each line of pixels represents a second in time. The researchers went on to experiment with a way to force the TV to play potentially unwanted content specified by the attacker.
"At this point, we have a possible attack vector into the home network or office through the Smart TV, which can be accomplished by hijacking DNS and serving malicious control data to the TV," they wrote. "Because the TV calls out to a control server by default and does not verify the authenticity of the control server, it allows an attacker in without the need for any incoming ports to be opened."
The researchers said that Vizio officials were responsive to the private vulnerability report Avast sent. Vizio has now issued a security update that fixes the problems. Avast said the patch should install on its own. Ars is skeptical of the claim of a self-installing update and curious to know what precautions Vizio takes to ensure that TVs install only authorized fixes, but we will give the manufacturer the benefit of the doubt.
Still, Wednesday's blog post is concerning, especially in light of last week's report that Vizio TVs track users' viewing habits and send them to advertisers. Equally troubling, the hack underscores the types of amateur goofs that Internet-of-Things developers routinely make. Secure programming is something that has taken companies like Microsoft, Apple, and Google years to perfect, and even now they all struggle. The approach of today's Internet-of-Things industry is to bolt a series of half-baked networking functions to an existing product and ship it as soon as possible. Until things change drastically, readers are better off foregoing the minimal benefits provided by an Internet-connected TV and settling for one with no networking at all.
reader comments
119