A recently disclosed vulnerability in Bind, the most widely used software for translating human-friendly domain names into IP addresses used by servers, makes it possible for lone-wolf attackers to bring down huge swaths of the Internet, a security researcher has warned.
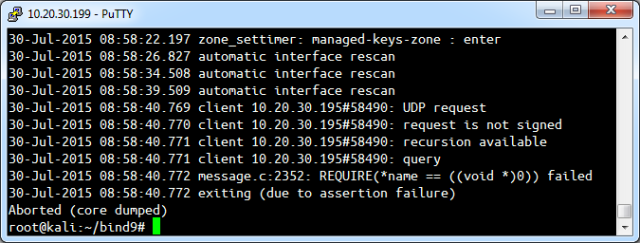
The flaw, which involves the way that Bind handles some queries related to transaction key records, resides in all major versions of the software from 9.1.0 to 9.8.x, 9.9.0 to 9.9.7-P1, and 9.10.0 to 9.10.2-P2. Attackers can exploit it by sending vulnerable servers a malformed packet that's trivial to create. Vulnerable servers, in turn, will promptly crash. There are no indications that the vulnerability is being actively exploited in the wild, and the bug wasn't disclosed until a fix was in place. Still, the critical vulnerability underscores the fragility of Bind, which despite its three decades in use and unwieldy code remains the staple for the Internet's domain name system.
Rob Graham, CEO of penetration testing firm Errata Security, reviewed some of the Bind source code and the advisory that Bind developers issued earlier this week and made this sobering assessment:
BIND9 is the oldest and most popular DNS server. Today, they announced a DoS vulnerability was announced that would crash the server with a simply crafted query. I could use my "masscan" tool to blanket the Internet with those packets and crash all publicly facing BIND9 DNS servers in about an hour. A single vuln doesn't mean much, but if you look at the recent BIND9 vulns, you see a pattern forming. BIND9 has lots of problems—problems that critical infrastructure software should not have.
Its biggest problem is that it has too many features. It attempts to implement every possible DNS feature known to man, few of which are needed on publicly facing servers. Today's bug was in the rarely used "TKEY" feature, for example. DNS servers exposed to the public should have the minimum number of features—the server priding itself on having the maximum number of features is automatically disqualified.
Normally, denial-of-service bugs receive low-severity ratings, but when they're present in servers that form the Internet's very core, the risks are much higher. Graham regularly scans almost the entire Internet to get an estimate of how many servers remain affected by the Heartbleed vulnerability in OpenSSL and other major software weaknesses. He said Bind's code base still isn't as bloated as that of OpenSSL, but it's much slower than it should be despite being written using C and C++. The result: Bind has all the security weaknesses that come with those programming languages without the speed that often justifies their use anyway.
Graham concluded:
The point I'm trying to make here is that BIND9 should not be exposed to the public. It has code problems that should be unacceptable in this day and age of cybersecurity. Even if it were written perfectly, it has far too many features to be trustworthy. Its feature-richness makes it a great hidden master, it's just all those feature get in the way of it being a simple authoritative slave server, or a simple resolver. They shouldn't rewrite it from scratch, but if they did, they should choose a safe language and not use C/C++.
reader comments
118